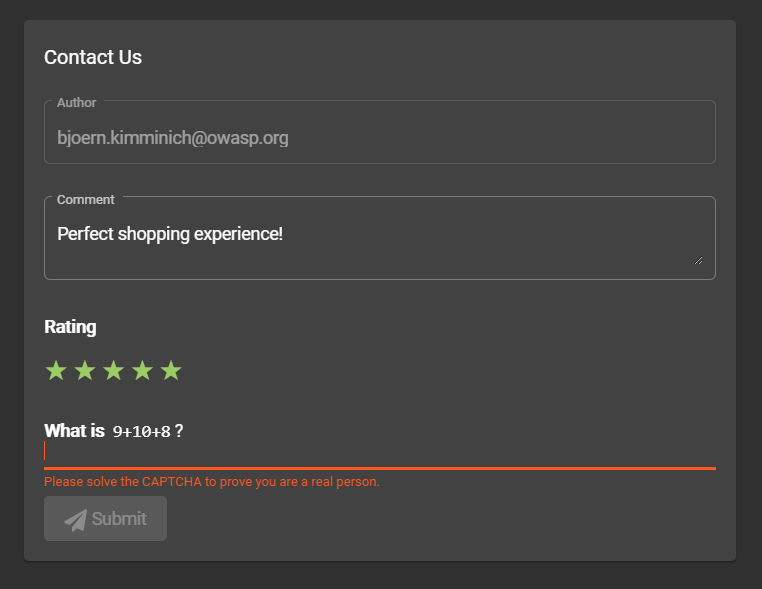
OWASP Juice Shop a Twitter: "We've been told that sometimes people grab our stickers and when they're home they already forgot what this weird leaky juice box actually stood for... ...that's why
GitHub - juice-shop/juice-shop: OWASP Juice Shop: Probably the most modern and sophisticated insecure web application
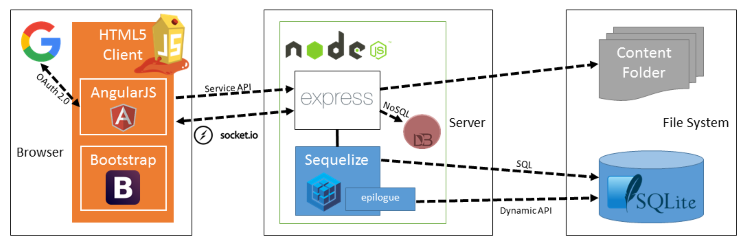
OWASP Juice Shop - An Intentionally Insecure Webapp For Security Trainings Written Entirely In Javascript
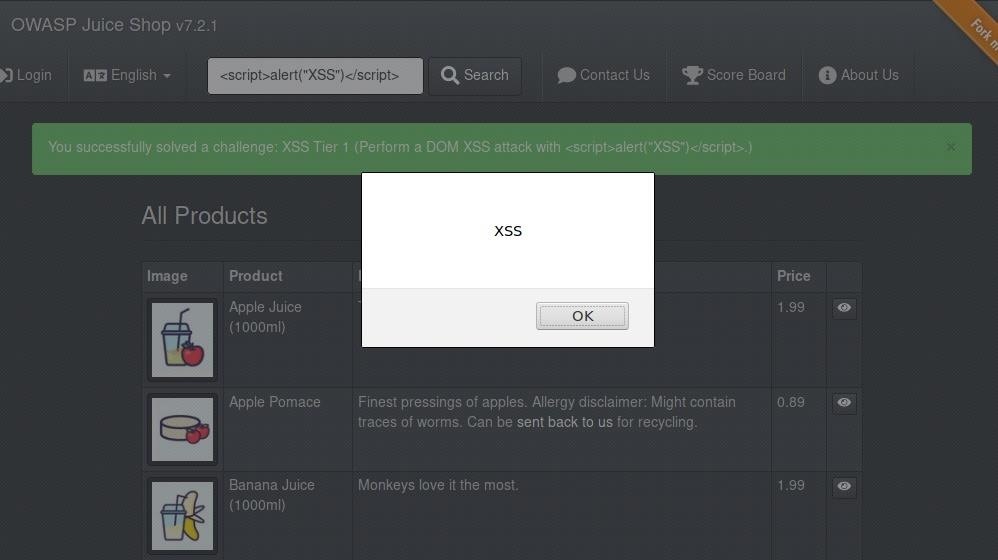
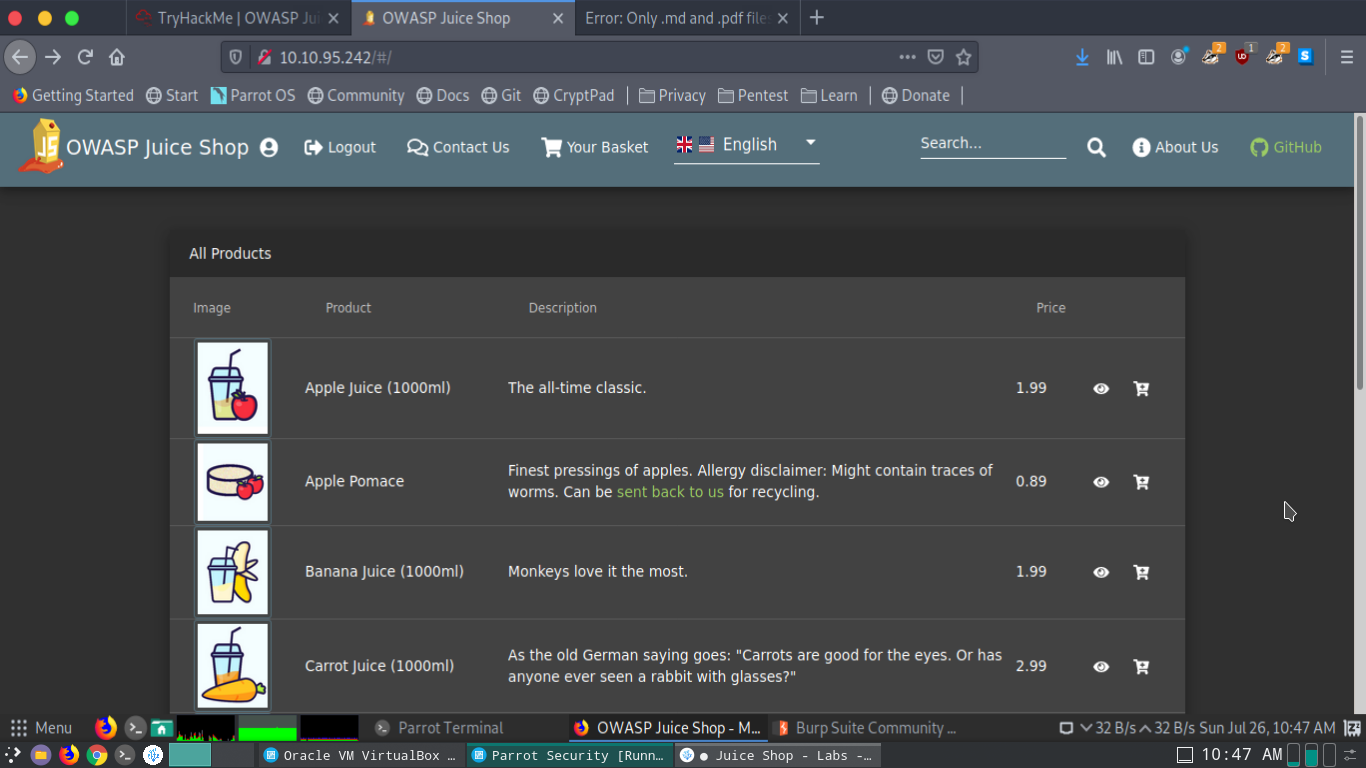
Beginner's Guide to OWASP Juice Shop, Your Practice Hacking Grounds for the 10 Most Common Web App Vulnerabilities « Null Byte :: WonderHowTo
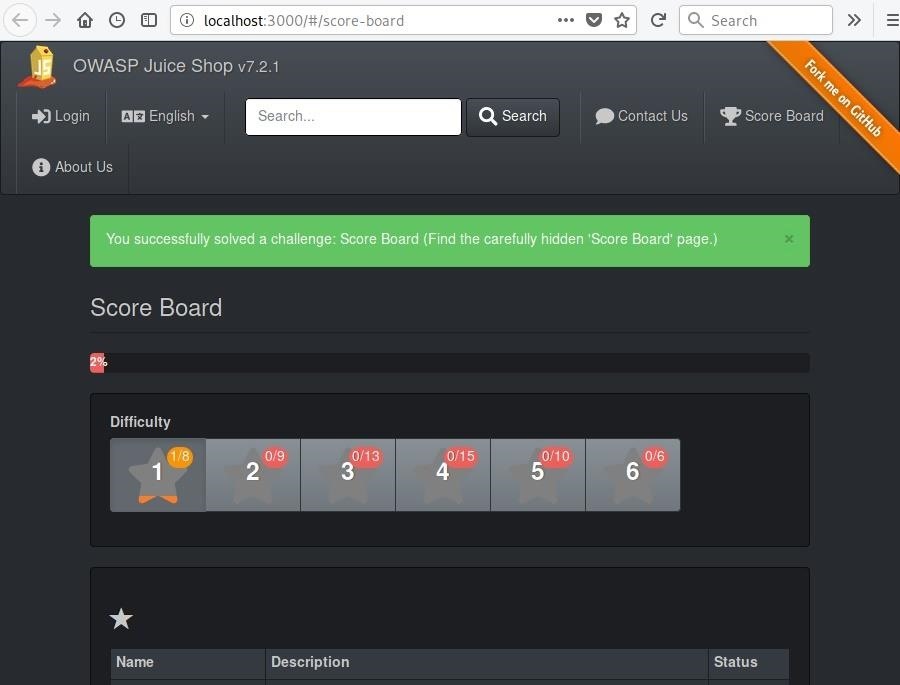
Beginner's Guide to OWASP Juice Shop, Your Practice Hacking Grounds for the 10 Most Common Web App Vulnerabilities « Null Byte :: WonderHowTo
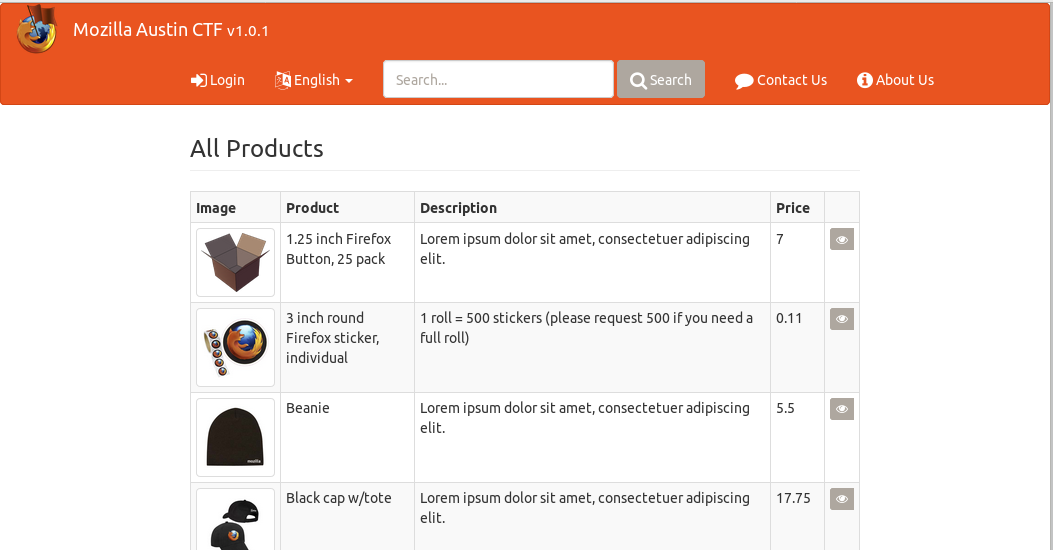
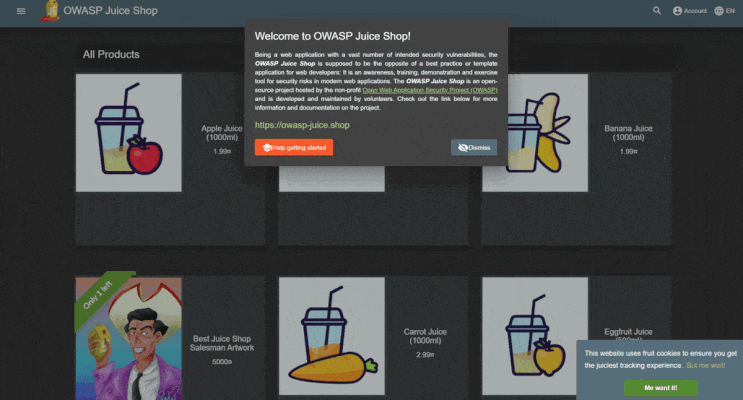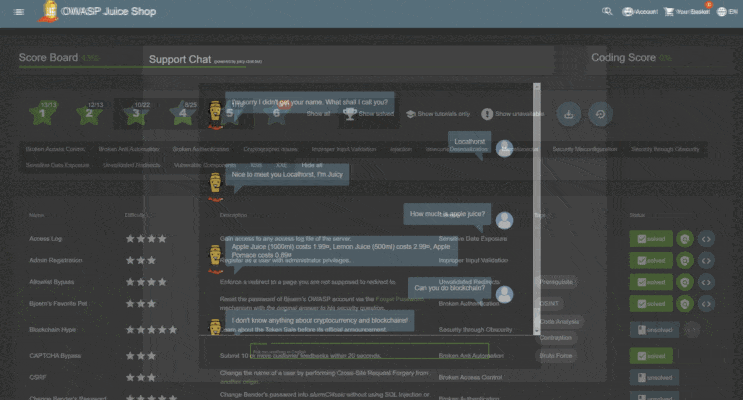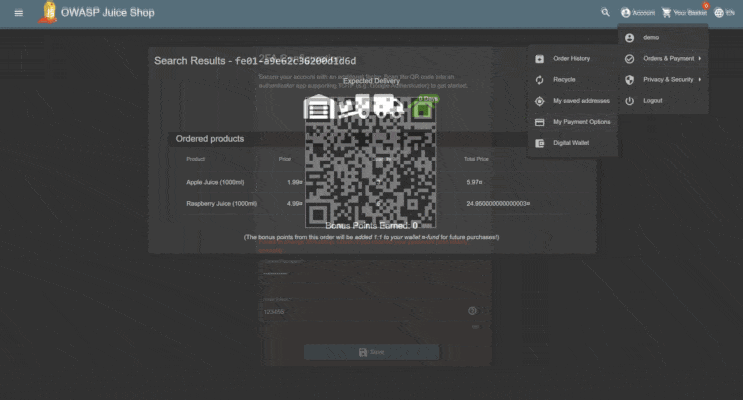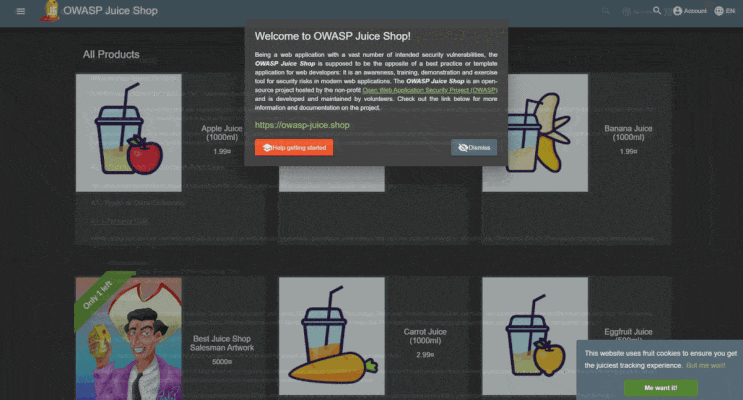
Hands-On Web Security: Capture the Flag with OWASP Juice Shop - Mozilla Hacks - the Web developer blog

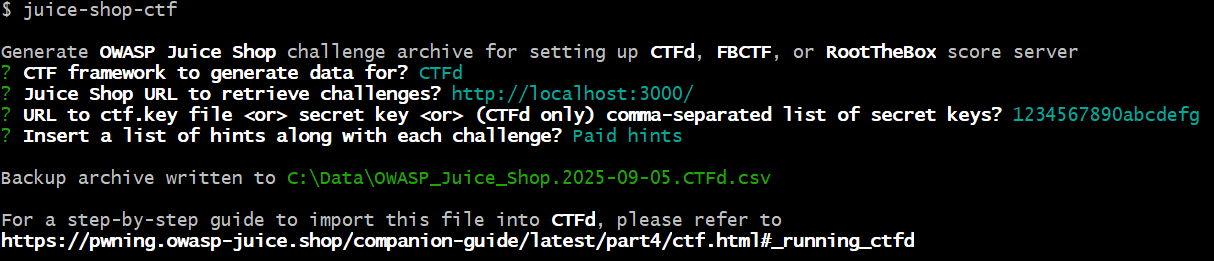
تويتر \ OWASP Juice Shop على تويتر: "The v7.0.0 release of juice-shop-ctf-cli adds @rootthebox to the list of supported CTF frameworks! The template even comes with its own embedded @owasp Juice Shop
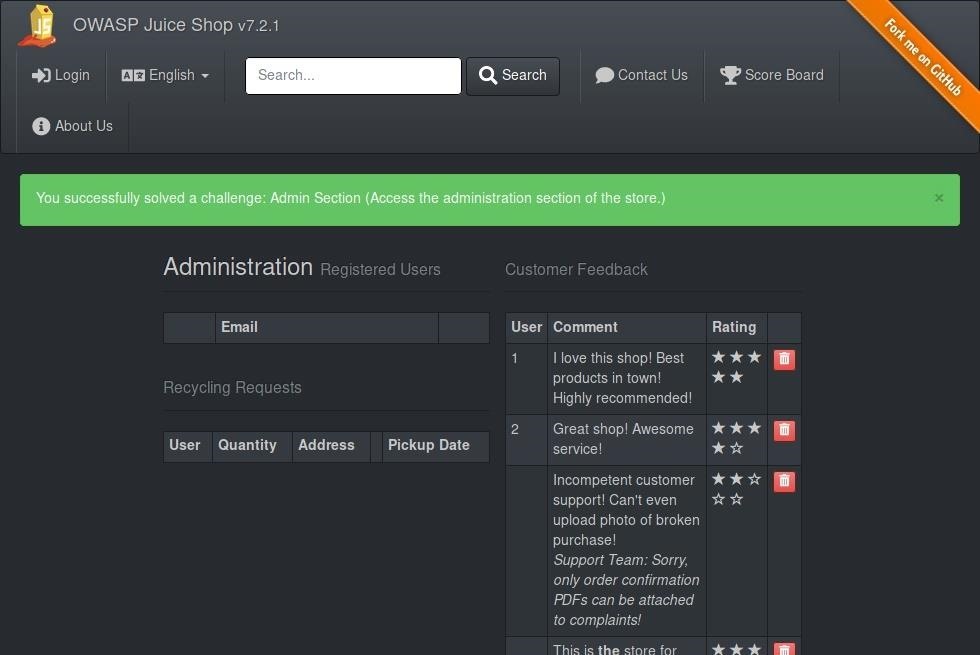

![REPO]@Telematika | bkimminich/juice-shop REPO]@Telematika | bkimminich/juice-shop](https://repo.telematika.org/images/project/bkimminich_juice-shop_hu2f1fcc90f48ec07e87921e9bfc4f3ebe_27139_900x500_fit_q75_box.jpg)